Blogs
Learn what subnetting in computer networking is and how to subnet IP addresses. This guide breaks down what a subnet mask is and how you can...

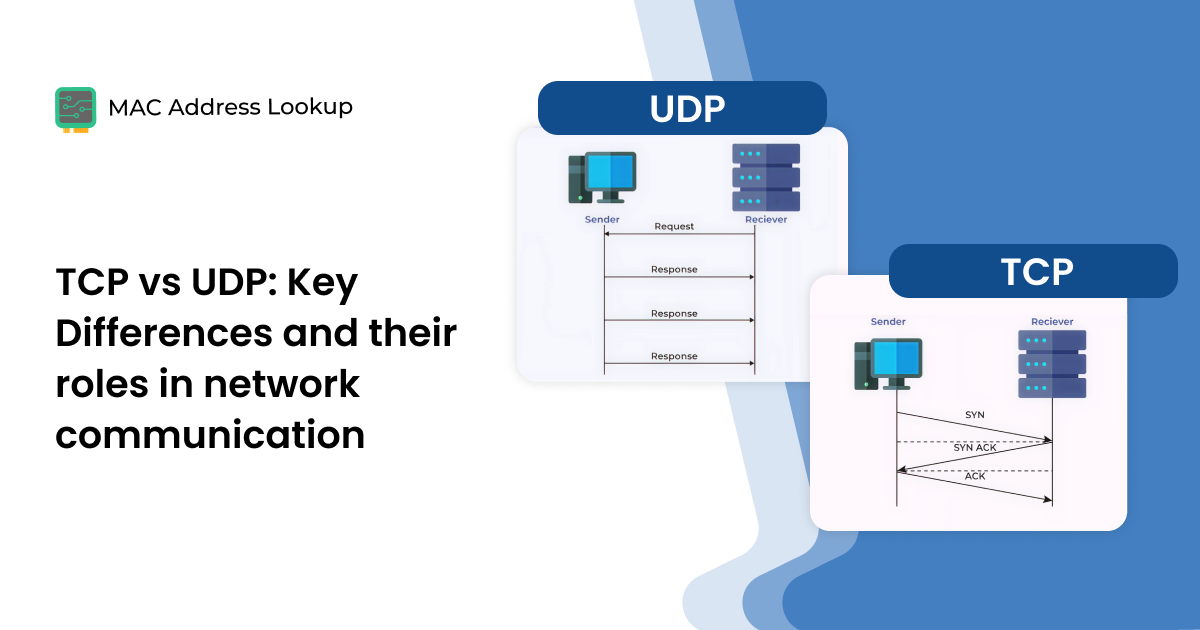
TCP and UDP are the backbone of how data travels across the internet. This guide breaks down how each protocol works, their key differences,...
Learn what a port number actually is and what it does. Explore different methods, simple and easy, for finding all the port numbers for a de...
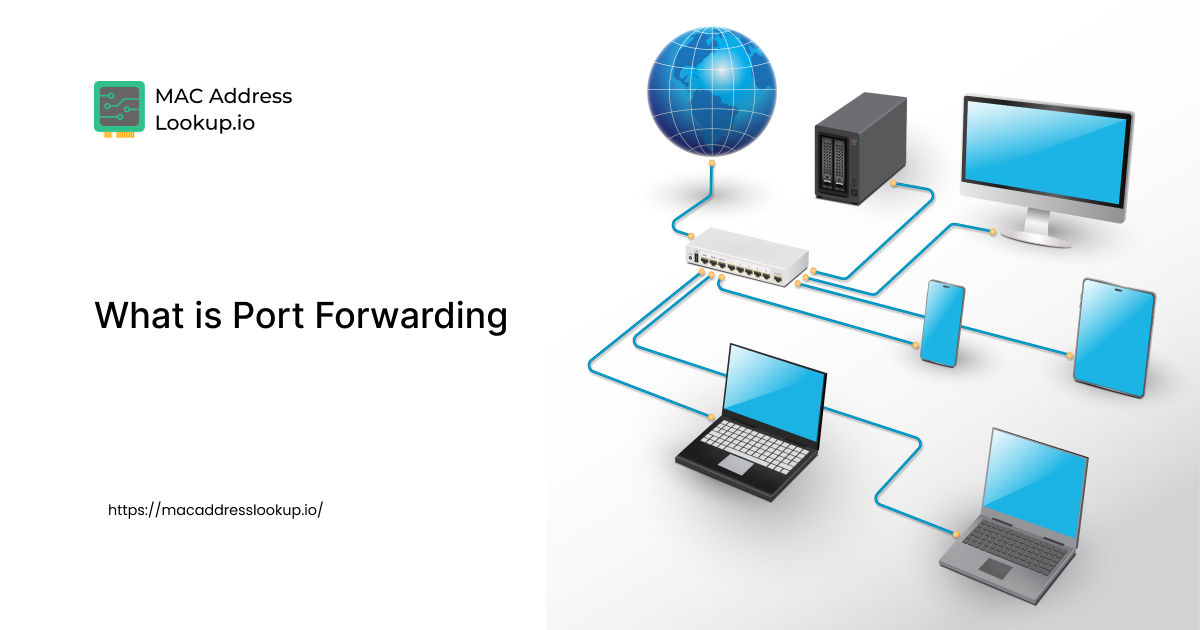
Learn how port forwarding opens specific pathways in your router to allow external devices to access services on your local network - secure...
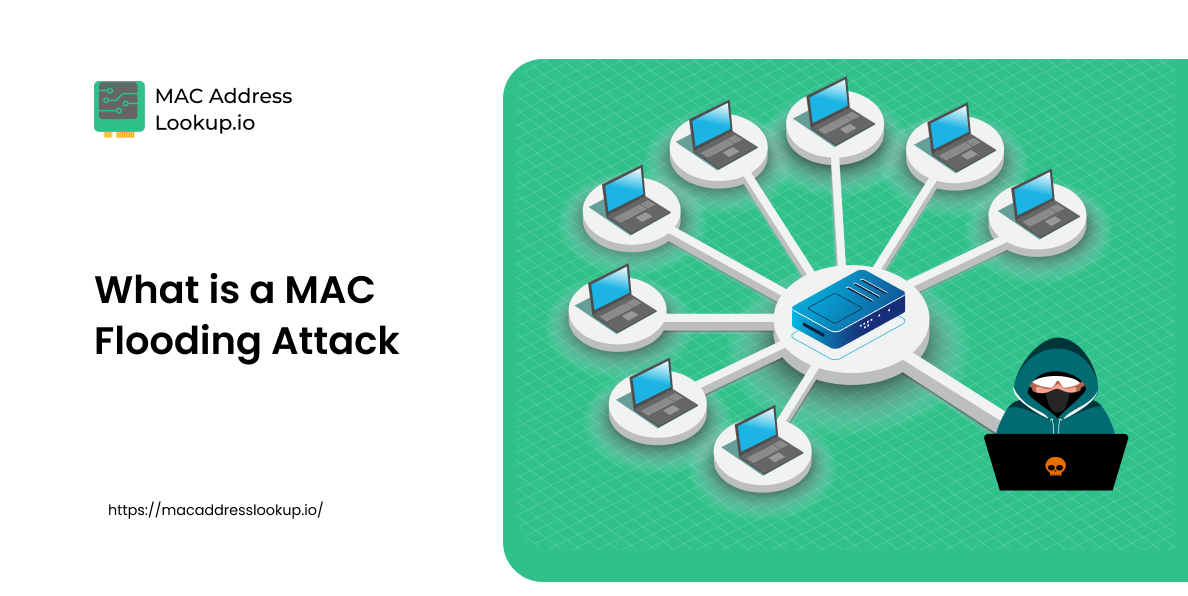
This guide explains how MAC Flooding attacks work, why they’re dangerous for your network, and the best ways to prevent them
Open ports can let hackers in - learn what they are, the risks they pose, and how to protect your system.

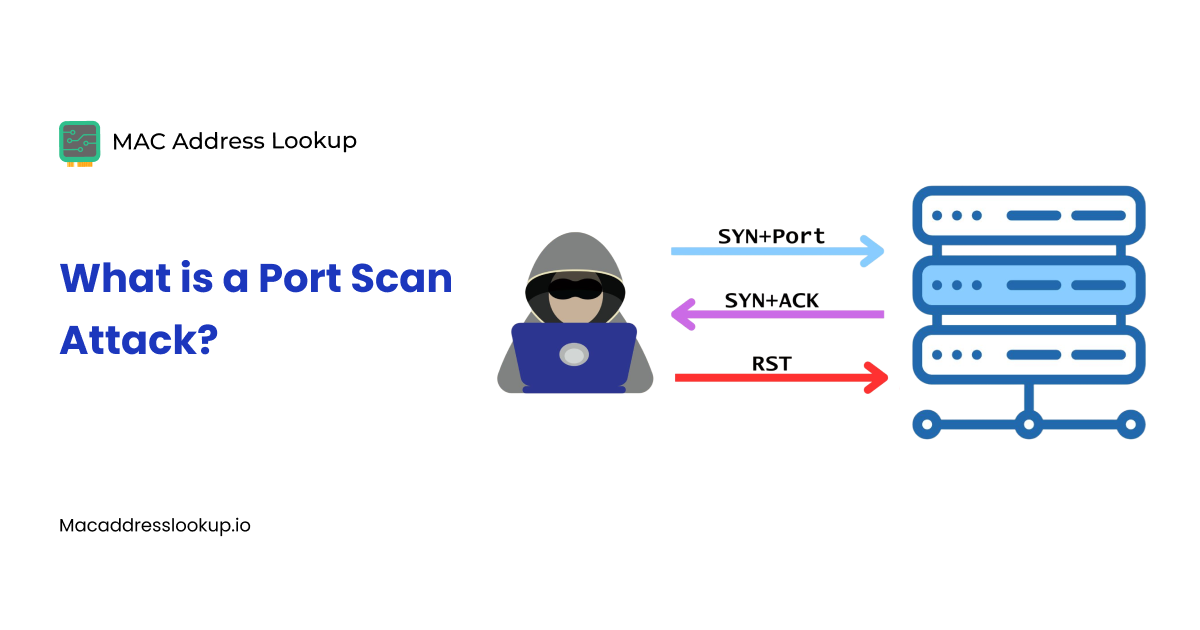
Discover how cybercriminals exploit port scanning to infiltrate networks. Explore ways to prevent this attack on your network.
A clear, easy-to-understand guide to the two types of MAC addresses and why they matter.

Learn how MAC filtering lets you control which devices can connect to your Wi-Fi, it’s like giving special access only to trusted gadgets.

Learn how hackers fake MAC addresses—and how you can stop them.
