What is a MAC Flooding Attack - All You Need to Know About
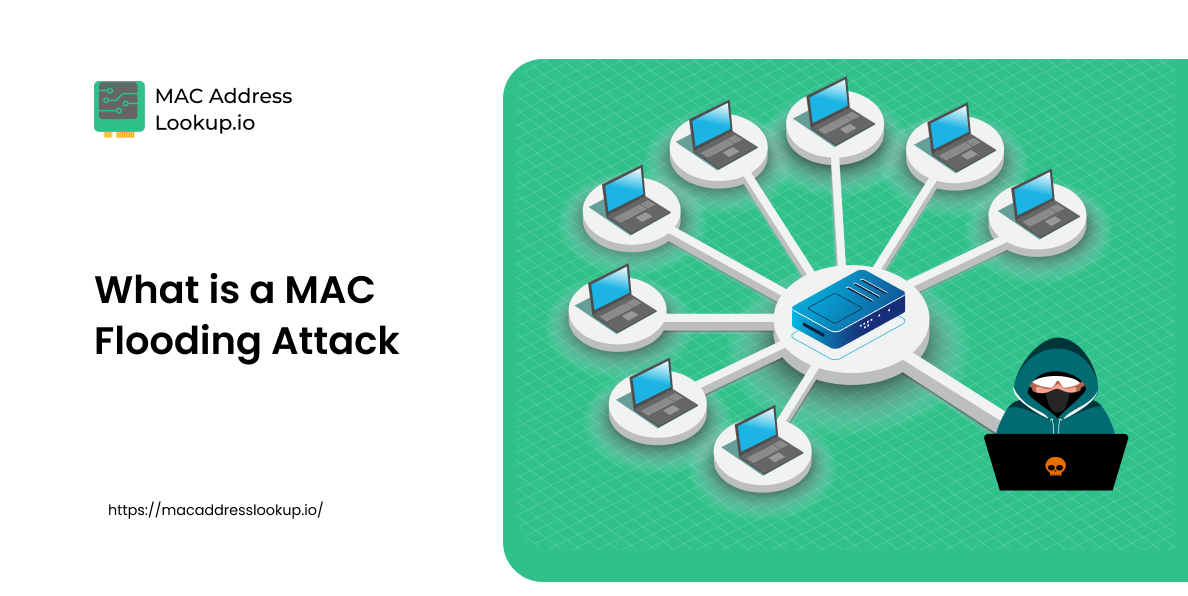
A MAC flooding attack is a type of cyberattack carried out by hackers to steal user data over a local network. Those networks that are on the internet are no exception to it. During this attack, hackers overwhelm the network switch with data packets.
A switch is actually a system that sorts the incoming data packets over a network and passes them to the relevant device. This blog post will provide you with all the information you need to know about a MAC flooding attack, including what it is, how it works, and more.
So, What Actually is a MAC Flooding Attack?
MAC flooding is a cyberattack carried out via the MAC (Media Access Control) address that is unique to every device. This address helps in identifying devices over a local network. Using these addresses (MAC), the devices are categorized, and connections are made with the relevant ports on a local network to transmit data.
The system that receives the data over a local network and passes it further to the correct port on the device is referred to as a switch. A switch holds a forwarding table (also called CAM Table) having all the matching MAC addresses for the physical ports listed in it.
When a switch receives data packets from a new MAC address, it adds that address to its forwarding table and links it to the relevant port, ensuring the smooth operation of services.
Hackers flood the CAM table with fake data packets in bulk using MAC spoofing or random addresses. When the CAM (content accessible memory) table gets filled, it reaches a point referred to as “Fail Open Mode”.
At this point, the switch will forward all the data packets it receives to every port it has, rather than just the destination port. This is how a MAC flooding attack starts.
How MAC Flooding Attacks Work (Step-by-Step)
For a deeper understanding, the following provides a step-by-step explanation of how MAC flooding attacks work in practice.
Attacker Connects to the Local Network
To launch the MAC flooding attack, attackers first connect to a local network. Note that MAC flooding can only be performed within the broadcast domain of a switch and cannot be executed remotely.
To gain access to the local network, attackers employ various methods. Common ones include:
- Physically plugging into an Ethernet port in an office
- Connecting to an unsecured or poorly segmented Wi-Fi network
- Exploiting a compromised internal device
Generate Random Source MAC Addresses
After connecting to a local network, the attackers generate a large number of random MAC addresses. They sometimes also spoof the original MAC addresses. These addresses are used as source MACs in Ethernet frames.
To achieve this, they utilize various black-hat tools. Using these addresses, they send data packets over the network in bulk. To the network, these data packets appear to be coming from different devices; however, in reality, they are all being sent from a single device.
Overwhelm the CAM Table
Attackers send data packets to the local network at a very high speed. As mentioned earlier, when data packets from a new MAC address appear, the switch adds them to the CAM table. But each CAM table has its specific limit.
Attackers continue to send fake data packets until the CAM table reaches its maximum capacity. And when that limit is reached, the switch will stop learning and adding new MAC addresses.
They also forget the previously stored MAC address due to rapid changes and reach a point referred to as “Fail Open Mode”.
Traffic Is Now Broadcasted
When the switch reaches the “Fail Open Mode,” it broadcasts all incoming traffic to all active ports. The reason is that it no longer knows where the real destination MACs are.
When this happens, all the users on the network will start receiving traffic segments that are not meant for them.
Moreover, devices will also start ignoring the source and destination of the traffic, except for the one device being operated by the hacker at the time.
Packet Sniffer is Used to Capture Data
Lastly, hackers utilize packet sniffers to analyze every Ethernet frame being broadcast. At this stage, the attacker can:
- View unencrypted emails, usernames, or passwords
- Monitor file transfers or internal communication
- Extract session cookies to hijack logins (if not encrypted)
If traffic is unencrypted, the attacker might also gain full visibility.
How Can You Detect a MAC Flooding Attack?
MAC flooding attacks can quietly compromise a network, so early detection is crucial. Below are some methods that help you spot such attacks before they cause severe damage.
1. Unusual Network Behavior
Unexpected network performance degradation is one of the most prominent signals for the said attack. As the switch broadcasts the data packets during the attack, the devices on the network will start receiving excessive traffic. This leads to slow internet performance and unexpected disconnections.
If your network slows down suddenly without any known bandwidth-heavy tasks, investigate immediately. Especially at Layer 2, which is crucial for a local area network (LAN).
2. Monitoring Switch Logs and CAM Table Changes
Managed switches keep track of MAC addresses in their CAM table. Under normal conditions, a MAC address maps to a specific port.
However, during the MAC flooding attack, many MAC addresses appear from one port. Or sometimes the table fills rapidly with random addresses.
Regularly monitor your switch logs and MAC address tables. If you notice frequent changes and repeated table overflow, your network might be under a MAC flooding attack.
3. SNMP Traps and Alerts from Managed Switches
Smart and managed switches support SNMP (Simple Network Management Protocol). By configuring SNMP traps, network admins can receive alerts when:
- The CAM table usage reaches the maximum capacity
- Suspicious traffic patterns are detected
- Ports exceed their allowed MAC address count (via port security)
If the SNMP alerts you, for instance, when the CAM table threshold is reached, immediately analyze the switch logs manually. If you notice anything suspicious, immediately take action, such as blocking the unknown MAC address or implementing MAC filtering.
How to Prevent MAC Flooding?
There are several strategies you can employ to prevent a MAC flooding attack. Below, we have shared some key ones among them.
MAC Filtering
MAC filtering allows you to define which addresses can connect to a network. By restricting access to known and trusted devices, you can prevent unauthorized or spoofed ones from connecting to your network.
But how can you know that the device trying to connect is reliable or a spoofed one?
Performing the MAC address lookup can benefit you here. It will let you identify the device manufacturer based on the MAC prefix.
If a device shows an unregistered vendor (such as those made using virtual machines), you can investigate further before whitelisting it.
Port Security
Managing port security is another way to defend against MAC flooding on your network. The port security feature is primarily available on managed switches. It allows you to limit the number of MAC addresses permitted on each port. When port security is implemented, it automatically disables/blocks a port in case any violation is detected.
Another important measure that helps prevent cyberattacks is regularly monitoring software ports on individual devices.
Why?
Because the unnecessary open ports make it easier for hackers to penetrate a network. They can be used to take over a device within a network and use it to do a MAC flooding attack.
To monitor what ports on your network are open, you can use our port checker tool. If your network device shows unexpected open ports, it could indicate a rogue system. And that system may be attempting MAC spoofing or other attacks.
Network Segmentation
Segmenting your network into VLANs (Virtual LANs) helps limit the scope of an attack. If a MAC flooding attempt occurs in one VLAN, its impact will be restricted to that segment only.
Proper network segmentation also helps ensure that sensitive systems, such as servers, are isolated from general user traffic. This will reduce their exposure to cybercriminals.
When you have implemented network segmentation, an attack will compromise only a single segment. The rest of your network will remain isolated.
Conclusion
A MAC flooding attack is a type of cyberattack in which attackers flood a network switch with data packets using fake MAC addresses. They overwhelm the network switch capacity, which, when done, broadcasts incoming traffic to all the ports instead of the dedicated ones. This way, only the MAC addresses used by hackers are accessible to the network, making it easier for them to harvest user data. However, by implementing the preventive strategies, you can protect your local network from MAC flooding attacks.