TCP vs UDP: Key Differences and Their Roles in Network Communication
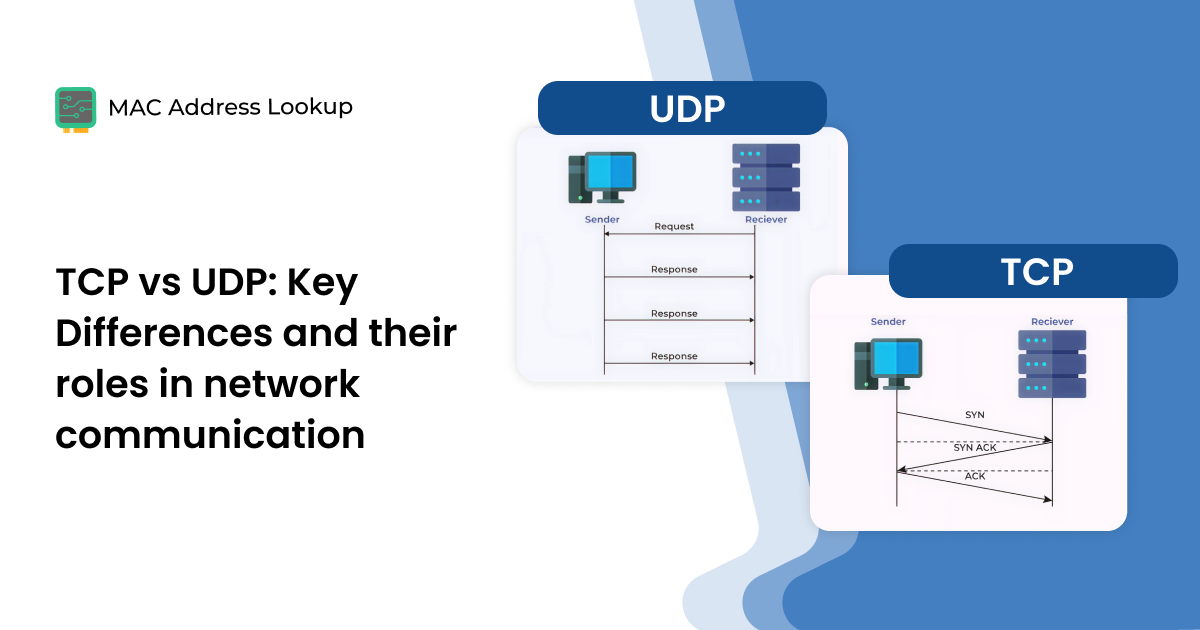
When you perform tasks online, such as loading a website or sending a message, two internet protocols come into play. Namely, these two protocols are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
Both these protocols belong to the Transport Layer of the TCP/IP model of the Internet protocol. TCP and UDP both ensure that your data travels across the internet, but they do operate on different principles.
This blog post will explain the difference between these protocols, as well as the role of each in network communication. But before we explain the difference, you must know about the nitty-gritty of the transport layer protocol.
So, let’s begin the discussion with that.
Transport Layer in the OSI and TCP/IP Models
The Transport Layer in the Internet Protocol is the intermediary between the Network Layer and the Application Layer. This protocol ensures reliable and organized communication between devices across various networks.
The primary role of this layer of the Internet protocols is to manage how the data packets are transmitted between the source and the destination system:
- Sent
- Segmented
- Transmitted
- Received
- Reassembled
The Transport Layer is the fourth layer (Layer 4) in the OSI (Open System Interconnection) Model. While in the TCP/IP Model, the transport layer is above the Internet Layer and below the application layer (usually second in the sequence).
To avoid any confusion: The Internet Layer in the TCP/IP model is somewhat equivalent to the OSI’s Network Layer.
As mentioned earlier, the primary role of the Transport Layer is to deliver data packets. Many people get confused here, thinking that the IP Layer (Internet Layer) is also meant to provide data packets.
The difference lies in the guarantees here.
Yet, the IP Layer also delivers packets from one host to another, but it does not guarantee the delivery. The Transport Layer, on the other hand, ensures the order and delivery of data packets across the devices and the networks.
The two primary protocols that help them here are TCP and UDP.
What is TCP (Transmission Control Protocol)?
TCP is defined as the Transport Layer Internet Protocol responsible for transferring data between devices and applications over the Internet. While transferring the data, TCP verifies the deliverability to the destination point.
In simple, TCP ensures that a connection is established between the devices and the server over a network.
How TCP Works?
TCP works in a three-step process, which is usually referred to as “three-way handshake. Upon the successful completion of all three steps, a connection is established between a device and the network.
The three-step process, or the three-way handshake of TCP, is as follows:
Syncrhronization ➡ Synchronization Acknowledgement ➡ Final Acknowledgment
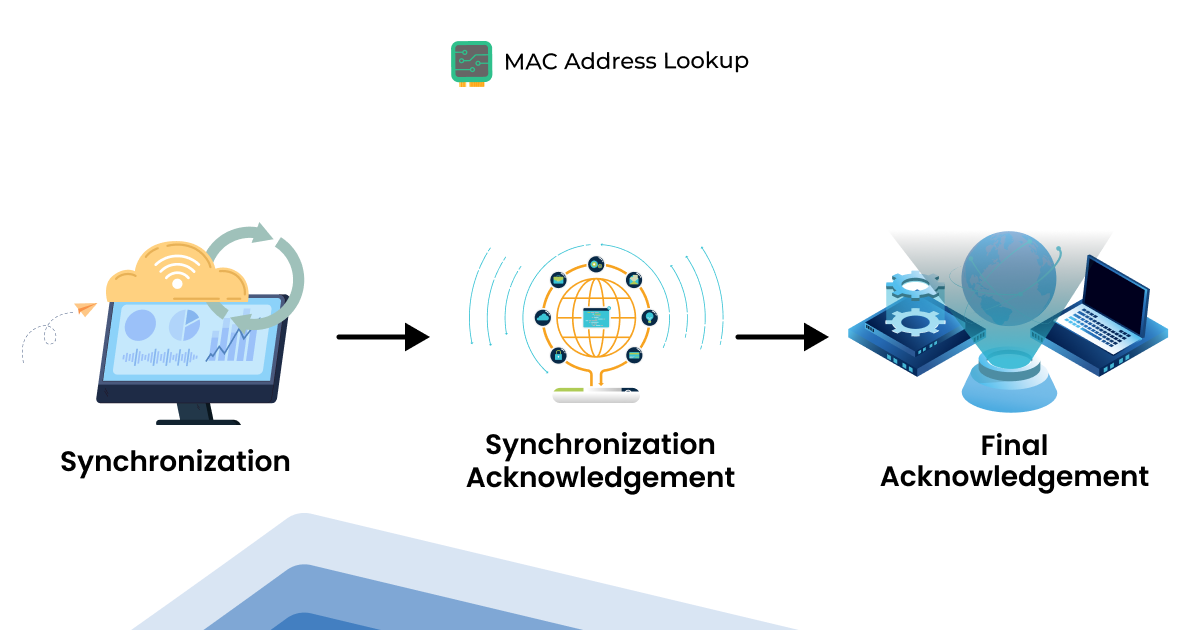
For a better understanding, the following explains how the three-way handshake works in practice.
1: Synchronization:
This process begins with the device initiating the data transfer request, also referred to as the “Client”.
During this, the “Client” sends a sequence number (SYN) to the server responsible for handling the request. In essence, it instructs the server to initiate the transfer of the data packet with this number.
2: Synchronization Acknowledgement:
The server acknowledges the SYN number sent by the client and, in return, sends a SYN number of its own.
3: Final Acknowledgement:
The client (device) acknowledges the SYN number sent by the server. And when the acknowledgement becomes successful, a connection gets established, beginning the data transfer.
Advantages & Disadvantages Of TCP
|
Advantages |
Disadvantages |
|
Establishes a connection between the client and the server. |
Uses more bandwidth and Slower than UDP. |
|
Operates regardless of the device's operating system. |
Prevent data from loading if a packet is lost. |
|
Supported by multiple routing protocols. |
Reduces transfer rate on congested networks. |
|
Guarantees data delivery and confirms after the data reaches the destination. |
Not suitable for multicasting and broadcasting. |
|
Fixed and unchangeable (tied to the hardware). |
Can be dynamic (changed by ISP) or static (manually set). |
|
Sends data while organizing it in a sequence. |
It is less efficient in low-latency local networks where reliability checks add unnecessary overhead. |
What is UDP (User Datagram Protocol)?
UDP is a communication protocol (message-oriented) that also transfers data between devices and networks. However, it does not guarantee or verify the data delivery. The UDP protocol is best suited for broadcast systems or applications that require real-time communication.
How UDP Works?
Whenever a device requests a data transfer, the UDP protocol immediately initiates the transfer without waiting for a connection to be established. The process remains in action until the data transfer is completed or terminated.
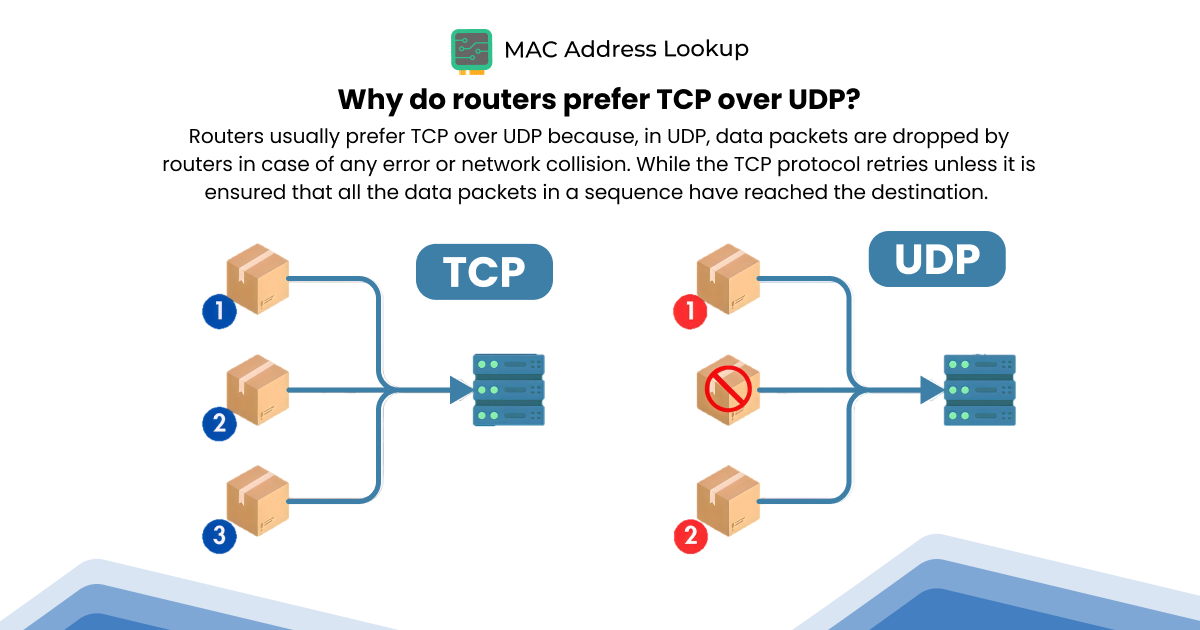
While transferring the data, UDP does not verify whether it has reached the destination point. It just keeps transferring the data, which is why UDP has a faster transfer rate than TCP. This is why you also hear of UDP as a fire-and-forget protocol. Moreover, the data transfer by UDP is also non-sequential. It is up to the receiver to organize the data and give it a sense of flow.
Advantages & Disadvantages of UDP
|
Advantages |
Disadvantages |
|
No need to establish a connection for data transfer. |
As no connection is involved, data transfer might be unreliable. |
|
Suitable for multicasting and broadcasting. It also transfer data in real time. |
There is no confirmation that the data has reached the destination point. |
|
Continues transmitting data without retransmission, even if some packets are lost during transfer. |
Drop data packets in case of any disruption or error. |
Now that you're familiar with the basics of both TCP and UDP, let's tackle a commonly asked question.
TCP vs UDP: Feature-by-Feature Comparison
For your convenience, we have shared a feature-by-feature comparison of UDP vs TCP in the table below. Going through this structured comparison helps to understand how TCP differs from UDP.
Additionally, it helps visualize how each protocol serves distinct purposes in network communication, depending on application requirements.
|
Feature |
TCP (Transmission Control Protocol) |
UDP (User Datagram Protocol) |
|
Reliability |
Reliable, as it ensures the delivery of all packets in the correct order. |
Unreliable, as there is no guarantee of delivery, or they arrive out of sequence. |
|
Connection Type |
Connection-oriented. It establishes a three-way handshake before data transfer begins. |
Connectionless. It sends packets directly without establishing a connection |
|
Speed |
Slower due to acknowledgment and sequencing. |
Operates faster because it transmits data without establishing a connection. |
|
Error Handling |
Retransmit data packets that might get lost due to errors. |
No retransmission of data packets occurs if they are lost due to an error or network congestion. |
|
Use Cases |
|
|
|
Header Size |
Larger (typically 20 bytes). |
Smaller (typically 8 bytes). |
Both TCP and UDP protocols operate over the IP Layer. However, their structural and operational philosophies serve different communication needs.
The comparison we performed so far entails the following:
- TCP emphasizes data reliability and integrity.
- UDP focuses on speed and efficiency.
When to Use TCP or UDP?
Choosing between TCP and UDP actually depends on the specific needs of an application.
TCP is ideal for applications where the following elements are critical:
- Data
- Integrity
- Order
- Reliability
TCP ensures that every packet sent is received exactly as intended. The table below represents the everyday use cases of TCP:
|
Use Case |
Reasoning |
|
Web Browsing (HTTP/HTTPS) |
TCP enables reliable web browsing by ensuring web pages load accurately and in the correct order. |
|
Email (SMTP, POP3, IMAP) |
TCP ensures that email messages are transferred without data loss. |
|
File Transfer (FTP, SFTP) |
Helps with the complete and accurate transmission of files for successful downloads or uploads. |
|
Remote Access (SSH, Telnet) |
Ensure sequential communication and that responses arrive reliably to maintain session control. |
UDP, on the other hand, is best suited for scenarios where speed and response times matter more than absolute reliability. This protocol is meant to send data continuously without waiting to establish connections. Nor will it wait for the acknowledgments. This is what makes UDP faster and more efficient for live applications.
|
Use Case |
Reasoning |
|
Streaming Media (YouTube, Netflix, IPTV) |
For online streaming, high speed is needed, and minor packet loss can be tolerated. That’s why UDP is preferred here. |
|
Online Gaming |
UDP facilitates immediate gaming updates and offers high responsiveness. |
|
VoIP and Video Calls |
Here, UDP helps with low latency to avoid distortion during calls. |
|
DNS Queries |
UDP helps with sending lightweight, single-request queries with minimal delay. |
In practical network design:
- TCP = Accuracy-focused (reliable, ordered, slower)
- UDP = Speed-focused (unreliable, unordered, faster)
Security Considerations for TCP and UDP
So, what we have learned so far is that both TCP and UDP play a vital role in network communication, right? Yet, both mentioned protocols are helpful, but they also come with certain cybersecurity risks. This is due to their fundamental design differences, with one being connection-oriented and the other connectionless.
Next, the most common security considerations for each protocol under discussion are explained individually.
Security Considerations for UDP
UDP works regardless of whether the connection is established, and the data deliverability is verified. This makes it vulnerable to certain forms of abuse, such as:
i: Port Scan Attacks
UDP ports are often used to identify open services through port scans. Port scanning attack is a common reconnaissance step in network attacks. Unlike TCP, which responds with RST packets for closed ports, UDP returns an ICMP "Port Unreachable or Timed Out" message when a port is closed.
That is why many network administrators use port checker to identify and promptly close unnecessary open ports, thereby reducing the space for attacks.
ii: DDoS Amplification Attacks
Since UDP does not require a handshake, attackers can spoof IP addresses. And while using the spoofed addresses, they send requests to open UDP services (like DNS or NTP). These services reply to the spoofed IP, overwhelming the victim with a massive amount of reflected traffic.
Security Considerations for TCP
Unlike UDP, the TCP protocol is connection-based. By default, it offers some inherent protections. But it also introduces some unique attack surfaces for cyberattacks.
i: Handshake Exploitation
In TCP, a 3-way handshake is used for establishing connections. Attackers can exploit this process by sending a flood of SYN requests. They disrupt the completion of the handshake.
This process is usually referred to as (SYN Flood Attacks). During this, server resources become overloaded, and the conditions resemble a Denial of Service (DoS).
ii: Session Hijacking
In TCP, session states are maintained. The data flows well, organized in number sequences. Sometimes hackers become successful in intercepting these numbers. And once done, they can impersonate themselves as a legitimate user or inject malicious data during an active session.
Bottom Line
TCP and UDP are both part of the Internet protocols that play a vital role in network communication. TCP facilitates reliable data transfer and verifies that the data has reached its destination. UDP, on the other hand, focuses on speed and efficiency. It helps power real-time applications such as online gaming, video calls, etc.
In this blog post, we explained the key differences between TCP and UDP. We hope that it helped you understand the differences. If you found this guide helpful, explore our other articles to deepen your understanding of networking.