What is a Port Scan Attack and How to Prevent it?
Every digital device that connects to a network has specific ports through which it communicates (sends and receives data) over the internet. These ports are dedicated to particular services or applications, each individually.
Some are called open ports, which let the traffic pass through and communicate. But some are called closed ports, meaning they won’t let the traffic pass through them.
Regarding open ports, they sometimes act as entry points for hackers. Using the port scanning attack, they penetrate networks and cause harm. In this blog post, you will learn what a port scan attack is and how to prevent your network from this attack.
So, What is a Port Scan Attack?
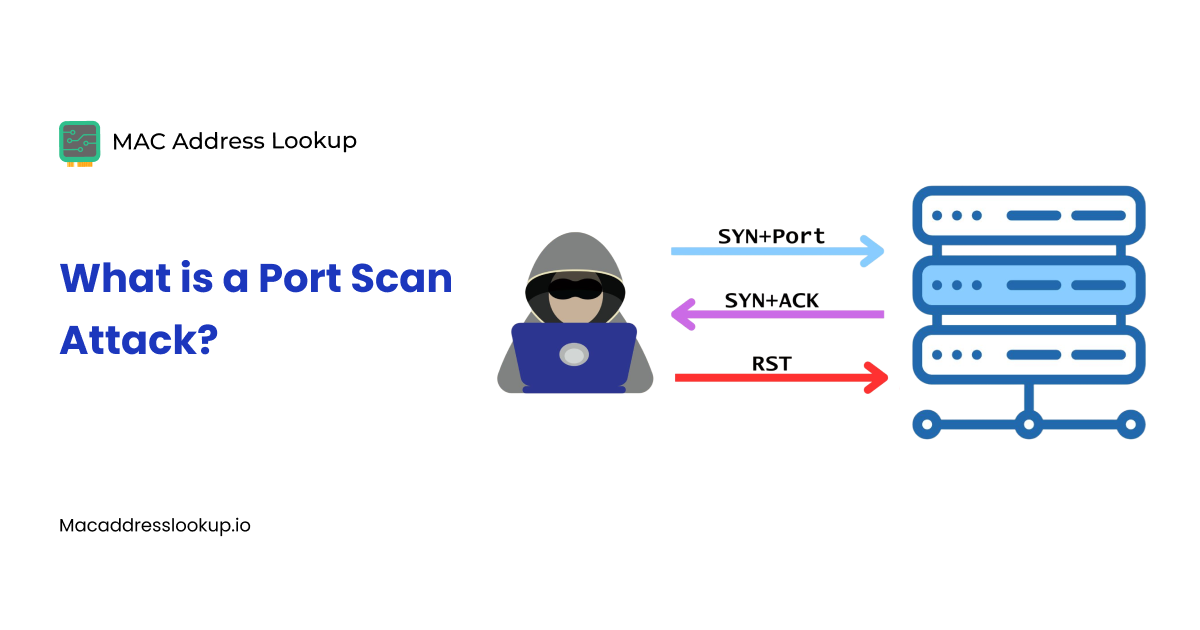
A port scan attack is not really an attack in itself. It is an investigative technique in which a hacker sends packets to multiple ports on a target device to determine which ones are open.
Open ports are the ones through which traffic is redirected to a service in use on a network. Hackers find vulnerabilities in the services using the ports and exploit them to infiltrate the network.
Signs of a Port Scan Attack
These types of attacks are quiet and quick. They often fly under the radar and go unnoticed because they don’t immediately cause harm. However, sometimes they leave some signs that, if monitored and judged correctly, can help you spot them.
Below are some common signs that show that your network is under a port scan cyber attack:
- Sudden increase in traffic over a network.
- High traffic over the ports that are not usually active.
- A single IP address is trying to attempt multiple ports simultaneously.
- Firewall rules are being triggered, e.g., many blocked attempts.
- IDS/IPS flagging suspicious port scanning activity.
Why is Port Scanning In Cybersecurity Dangerous?
Yet, a port scan seems a simple way to check what ports on a network are open and closed. However, many cybersecurity experts consider port scanning activity dangerous and refer to it as the first step in hacking.
When a port scan is performed, it exposes which network ports are open and running services. Some advanced port scanners can even expose the versions of the services using that port.
If a hacker finds a vulnerability in any of these services (e.g., outdated or unpatched), they can exploit it to gain unauthorized access to the network. Moreover, they can also carry out other attacks such as:
- DDoS attacks target exposed services
- Ransomware deployments via weak remote access ports
- Credential stuffing on login-enabled ports like RDP or SSH
Moreover, some automation tools developed by hackers automatically exploit the vulnerabilities in open ports. This further leads to
- Remote code execution
- Privilege escalation
- Full control of the target system
How to Prevent Port Scanning Attacks?
Below are some ways cybersecurity experts suggest to prevent port scanning attacks.
-
Scan Before the Attacker
The most suggested thing to network administrators is to perform port scans on their own from time to time before hackers do. This scan can easily be performed using our port checker.
Why? To identify any vulnerabilities or any unnecessary ports that are left open. In the case you do identify such ports, close them immediately. This will help you in closing the entry gate for hackers.
-
Deploy Secured Firewalls
By deploying a secure firewall, you can track the traffic of open ports. This will help you spot and block any unusual traffic. However, you cannot block all the ports using a firewall.
Firstly, blocking all is impossible due to TCP/IP rules. If you manage to block all, it will also block all the traffic communication. To avoid this, an adaptive firewall is recommended. They will block a port only when a suspicious activity is observed.
-
Use TCP Wrappers
TCP wrappers help in monitoring the data packets incoming to a network. They only permit those who are authorized and verified to communicate. All the rest will be rejected for communication.
-
Enable Port Knocking or Single Packet Authorization (SPA)
Port knocking is another stealthy method for preventing port scanning attacks. It keeps ports hidden until a specific sequence of connection attempts is made. This helps in avoiding open ports from being scanned. Only users who know the “knock” sequence can access the service.
Wrapping Up
Port scanning checks what ports are open and actively running on a network. This is usually considered as the first step for cybercriminals to carry out a more advanced attack.
In a port scan attack, they first find the open ports of a network, then find vulnerabilities in them, and then exploit them to penetrate the network and get unauthorized access to user data.
However, by following the prevention strategies we discussed in this blog post above, you can protect services on your network from a port scanning attack.