What Are Open Ports? Understanding Security Risks & Ways to Protect

In networking, ports are logical endpoints that enable a device to identify the processes or services running on another device. In simple terms, these logical points enable devices to communicate with each other.
However, not all ports on a device accept connections, or, in other words, traffic. Those that do not accept are referred to as closed ports. However, some devices receive traffic and allow them to communicate. These are referred to as open ports. Open ports always come with some security risks.
In this blog post, you will learn what open ports are, the associated security risks, and ways to protect them.
What Is an Open Port on a Network?
An open port is a networking port configured to accept incoming and outgoing connections. For this, connections use various protocols such as TCP and UDP. In contrast, there are closed ports that do not accept connections and ignore them.
When a port is open, a particular port number on the device is assigned to it, which makes it accessible to connections. This port number actively listens for incoming connections and lets the devices communicate.
Whenever the communication is TCP or IP-based, ports are an integral part of it. All the services running on a device, such as web browsers, emails, file transfers, etc, perform their activities (send or receive data) via ports.
Know that a single port can be dedicated to a particular service and not be used for other services. The purpose is to align conflicts.
As an example:
- Port 80 is used for HTTP traffic and cannot be used for HTTPS traffic.
What Are Open Ports Designated For?
Open ports are designated for communication purposes between devices or servers. By communication, they send and receive the data via these ports. Every single port assigned to a service or application listens to the traffic (both incoming and outgoing).
In simple terms, think of these ports as the digital gates that let a local network communicate over the Internet. These ports play a vital role in network communications, especially when carrying out multiple tasks on a device.
As an example:
Suppose you are working online in a browser, and at the same time, you have opened YouTube in another tab, listening to songs. In such cases, your device connects with the servers simultaneously via separate open ports.
Why Are Open Ports Dangerous?
Whenever you read/hear about open ports, you often hear that they are dangerous. Well, inherently, they are not harmful. They are meant to facilitate communication between the devices and the services.
But sometimes these ports get misconfigured or become insecure. This is the case when they become dangerous.
Why?
Because when they get misconfigured, open ports expose the data related to the service to the outside world, including cybercriminals.
The following reasoning will help you understand “Why Dangerous” better.
Exposed Services to Attackers
An open port means a service is actively listening for connections. If that service is vulnerable or misconfigured, attackers can exploit it for various purposes.
For example, they will try to gain access, execute code, or disrupt operations using these ports.
Every open port that is misconfigured or vulnerable is an entry point for attackers. The greater the number of open ports, the greater the chances of cyberattacks.
Risk of Unauthorized Access
Hackers often identify open ports on networks and find the weak points. They can easily be exploited if they see weakness in some services, such as Remote Desktop (RDP) or SSH. Hackers can gain complete control of the system if access is not restricted in time.
Targeted by Malware and Worms
Many viruses and worms exploit specific ports (e.g., WannaCry used SMB on port 445). If these ports are open and unpatched, malware can spread rapidly across systems and cause disruptions.
How to Find an Open Port on a Network?
There are many ways you can check an open port on a network. You can use command-line tools on your operating system to identify them. But the process is a bit technical. However, there is a simple way as well. That is using the port checker by Macaddresslookup.io.
Here’s how you can do that:
- Visit Macaddresslookup.io.
- Navigate to the port checker tool.
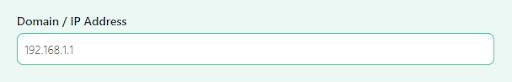
- Enter the domain or IP address in the designated field.
- Choose the port type (server, game, application, P2P) or check custom ports.
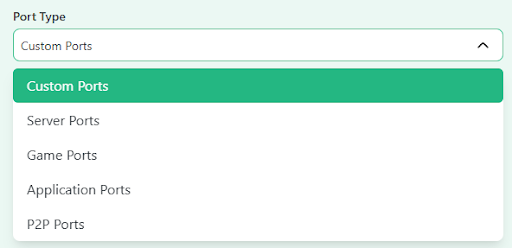
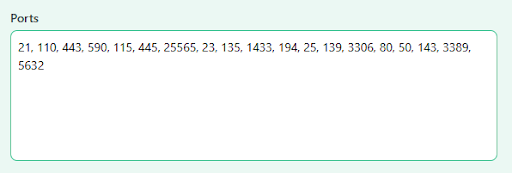
- Add port numbers individually separated by commas in the “Ports” box (in case you want to check custom ports). You can also select them from the list on the right side.
- Click check.
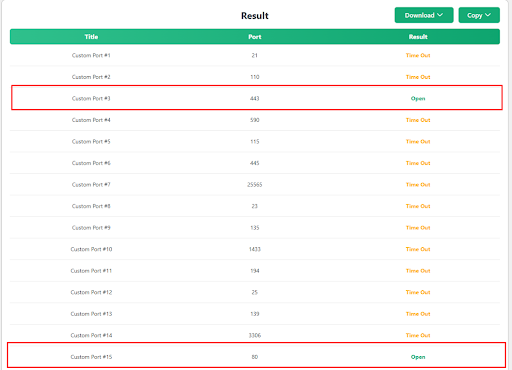
Within seconds, the tool will scan reports and show you the results in a table as in the one we shared below.
See the above table for yourself. The ports whose results show “Open” are the open ports, and those that show “Time Out” are closed.
What to Do After Finding Open Ports?
Once you have identified the open ports on your network, the next step is to find what services are running on these ports. Then, verify that all these open ports are secure and have no vulnerabilities.
How to Secure Open Ports?
The following are some ways to secure open ports on a network and protect them from cybercriminals.
-
Network Segmentation
Implementing network segmentation is a good practice to secure open ports. Your network is divided into small subnets with different IP addresses for segmentation. Even if hackers penetrate a segment, they cannot simply penetrate the rest. This helps reduce the risk of ports being compromised.
-
Close Unused Ports
Conduct port scans occasionally to keep yourself updated on what ports are open. If you find that some unnecessary ports are set to open, immediately close them. This will help in reducing entry points for malicious actors or malware.
-
Use Firewalls
Using firewalls is another good strategy to secure open ports. Firewalls are meant to control a network's incoming and outgoing traffic. If someone unauthorized tries penetrating an open port, the firewall will block them and only let authorized traffic pass through.
-
Enable Multi-factor Authentication
Multifactor authentication (MFA) is a way in which a user has to provide more than one verification to access the network services via ports. It acts as an additional security layer for open ports and is very beneficial.
-
Use VPN
VPNs (Virtual Private Networks) only allow authenticated users to access network services via encrypted tunnels when enabled. They hide and shield the open ports from public exposure, reducing the surface for hackers to penetrate.
Wrapping Up
Open ports on a network are configured to access services on a network. Each port is assigned to a particular service individually. When exposed to the public, they are targeted by malicious actors. Using them, hackers or malware can penetrate the network and create problems. However, following the strategies we shared in this blog post, you can secure your open ports from cybercriminals.